Authentication & Authorization
BoilStream includes a built-in Web Auth GUI for user authentication and platform administration. Access it at https://your-domain/.
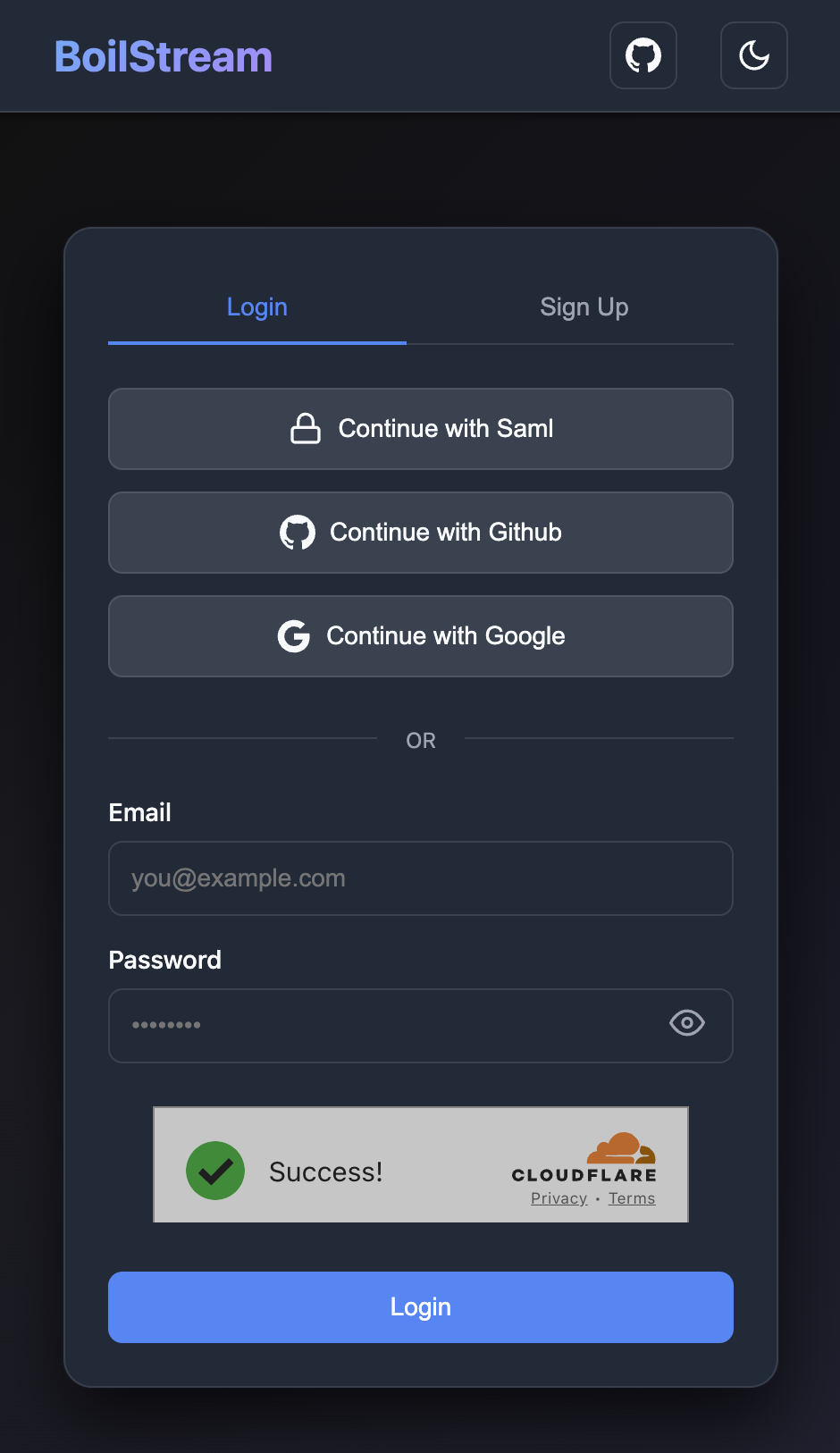
Two Dashboards
User Dashboard (after login):
- Get PostgreSQL credentials for database access
- Get JWT tokens for HTTP ingestion API
- Manage MFA settings (TOTP, passkeys)
- View active sessions
Superadmin Dashboard (username: boilstream):
- Cloud accounts (AWS, Azure, GCP credential management)
- S3 bucket registry
- BoilStream roles (IAM-like access control)
- Role assignments to users and SAML groups
- DuckLake catalog management with ownership transfer
- User management (list, delete with cascade)
- SAML SSO configuration (metadata upload, attribute mapping)
- SCIM user provisioning
- Cluster management (brokers, leader stepdown)
- Audit logging and cloud log forwarding
Features
- Multiple Auth Methods: SAML SSO, GitHub OAuth, Google OAuth, Email/Password
- Credential Vending: PostgreSQL credentials + JWT tokens for HTTP ingestion
- Role-Based Access Control: Map SSO groups/teams to database permissions
- Multi-Factor Authentication: TOTP, passkeys, backup codes
- Industry Standard Encryption: User and superadmin databases encrypted with AES-256-GCM
- Session Security: HttpOnly cookies, CSRF protection, configurable TTL
Quick Start
- Enable auth server in
config.yaml:
yaml
auth_server:
enabled: true
encryption_key_path: "encryption.key" # Auto-generated
session_ttl_hours: 8Configure authentication:
- SAML SSO: Via Superadmin GUI → Entra ID guide
- GitHub/Google OAuth: In
config.yaml→ Full guide - Email/Password: Enabled automatically
Configure authorization:
yaml
auth:
authorization_enabled: true
admin_groups: ["Admins", "12345678-1234-1234-1234-123456789abc"]
write_groups: ["Data Engineers"]
read_only_groups: ["Analysts"]- Start server (first run prompts):
bash
./boilstream --config config.yaml
# First run prompts:
# 1. Enter encryption key (press Enter to auto-generate)
# → Saves to encryption.key (if path configured)
# 2. Set superadmin password (min 12 chars)
# → Creates superadmin account (username: boilstream)
# Access Web GUI: https://your-domain/Database Encryption
User and superadmin databases encrypted with AES-256-GCM. On first run, BoilStream generates a 32-byte encryption key (or prompts you to provide one). If encryption_key_path is configured, the key is saved for automatic loading on subsequent starts.
What Users Get
After login, dashboard shows:
- PostgreSQL credentials (host, port, username, password, expiry)
- JWT token (for HTTP ingestion API)
Next Steps
- Web Auth GUI - Complete setup guide
- Entra ID SAML SSO - Microsoft Entra ID integration